Secure Encounter-based Mobile Social Networks: Requirements, Designs, and Tradeoffs
₹3,500.00
10000 in stock
SupportDescription

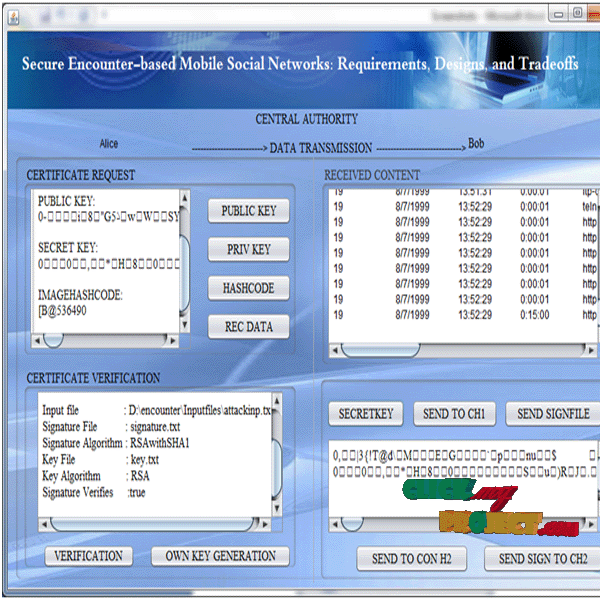
Encounter-based social networks and encounter-based systems link users who share a location at the same time, as opposed to the traditional social network. In this paper, we provide the functional and security requirements for these new systems, such as availability, security, and privacy. In our design, we use the X.509 standard for certification without any modification to the structure of the certificate, but limit the attributes in the certificate to preserve the privacy of our users. Our certification and visual authentication schemes are very simple. Here, we consider two design schemes. 1. Immediate Key Exchange 2. Delayed Key Exchange. First, an sender generates a pair of public and secret keys (PK,SK), computes the hash value of her own image and other relevant information to a certificate request, and sends it to a signing authority. Second, the signing authority checks the validity of the metadata in the certificate request and verifies the validity of relation with the certificate. If the verification process is successful, the signing authority signs the certificate using its own private key and sends to sender. In Receiver side tries to verify if the certificate along with the photo have a valid signature from a trusted authority. Receiver computes the hash of the photo and other information sent by sender, comparing it to the value embedded in the certificate. If the signature is valid, then the data transmission is occurring between the sender & receiver. In Immediate Key Exchange process, each user in the vicinity will detect the transmission and attempt to decrypt it & also it is time based process, when the user gives acknowledgement to the sender. However, only the target user will be able to decrypt the message correctly. In Delayed key exchange process is a time released process, the user public key & image are send to the user, here also only the target user will be able to decrypt the message correctly & there by providing better security in communication process.