Resilient Authenticated Execution of Critical applications in Untrusted Environments
Our Price
₹2,500.00
10000 in stock
Support
Ready to Ship
Description
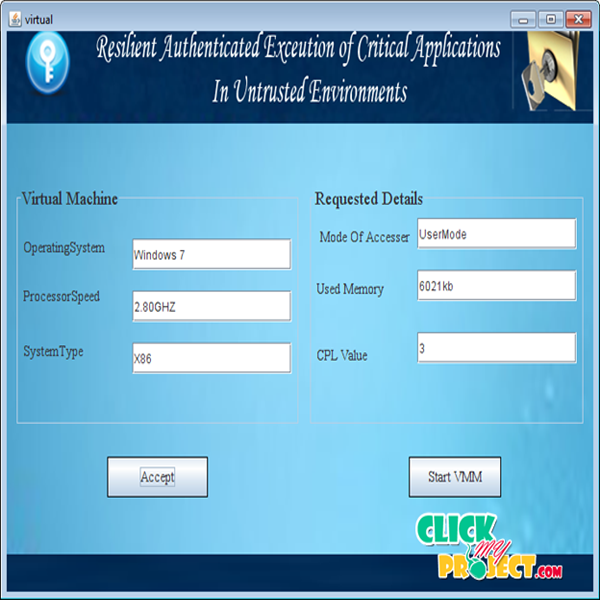
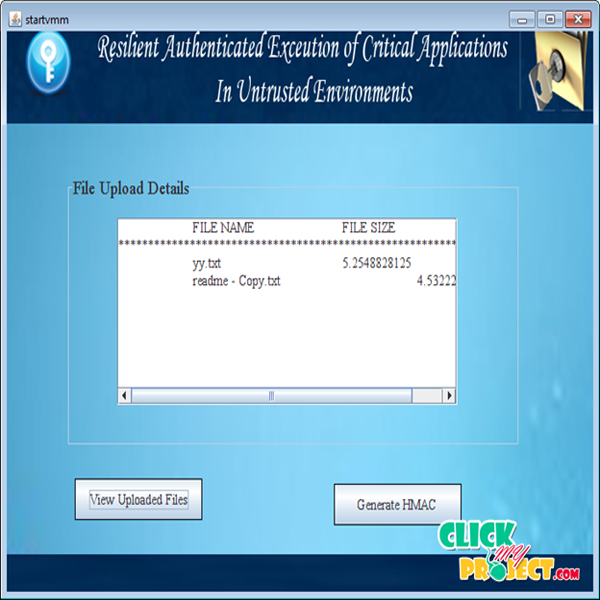
In this resilient execution environment can be developed for a critical application even in the presence of corrupted application. If the attacker tries to access the application content by corrupting when an Application is executing. In previous case the attacker corrupts the application by injecting code then the application terminates immediately without executing it. In our current system even in the presence of corruption the application is executed without any interception and it provide a resilient authenticated execution of critical application in entrusted environment by using Virtual Machine Monitor (VMM). VMM is a monitoring technique to monitor all the activities during execution and it is one of the best recovery schemes to identify any corruption occur at the time execution. It repairs the memory corruption and allows the process for normal execution. VMM solutions generally broadcast into two categories they are memory authentication and memory duplication. Memory authentication is to check the integrity of an application and memory duplication is to rectify the corruption.
Tags: 2012, Java, Security Projects