Improving Security and Efficiency in Attribute-Based Data Sharing
₹2,500.00
10000 in stock
SupportDescription
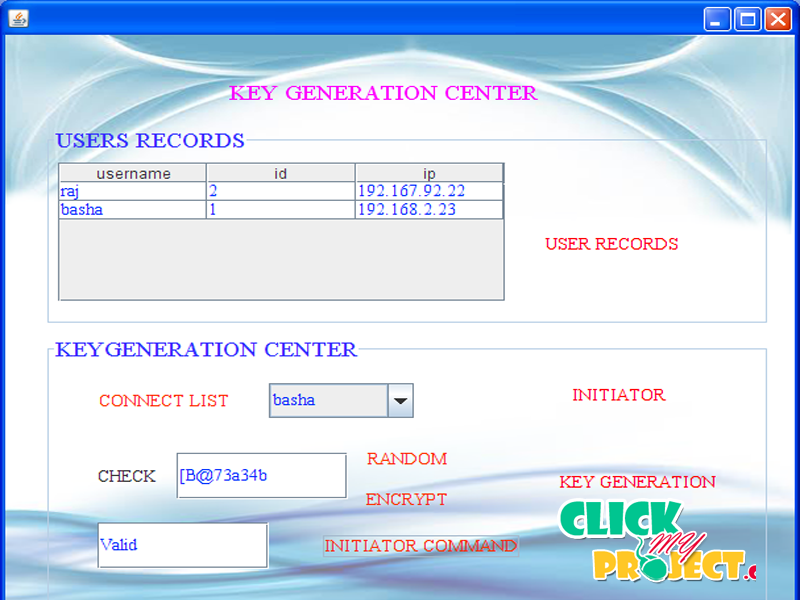
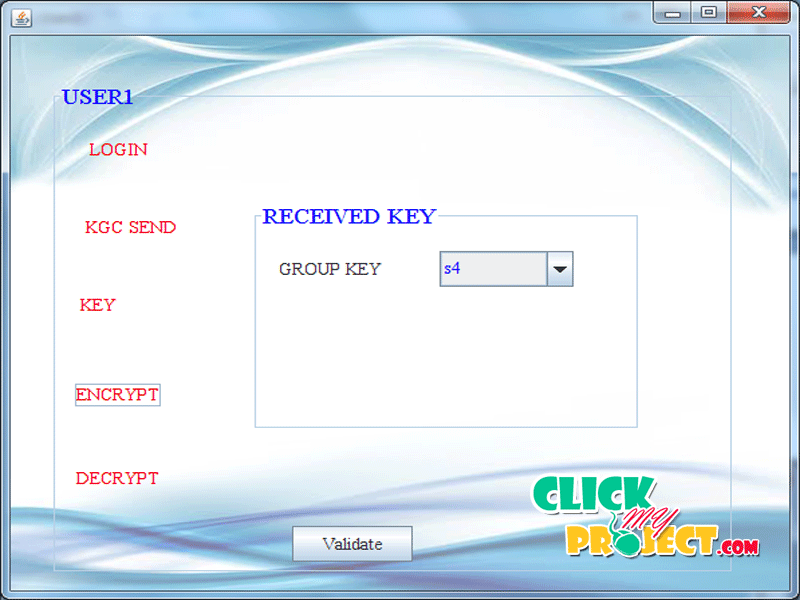
Key transfer protocols rely on a mutually trusted key generation center (KGC) to select session keys and transport session keys to all communication entities secretly. In order to ensure secure communication, before exchanging communication messages, a key establishment protocol will distribute one-time secret session keys to all participants, which needs to provide confidentiality and authentication for session keys. Most often, KGC encrypts session keys under another secret key shared with each entity during registration. the existing group key transfer protocols based on secret sharing all use threshold schemes that need to compute a -degree interpolating polynomial to encrypt and decrypt the secret group key, then it increases the computational complexity of system. In this paper, we propose an authenticated key transfer protocol based on secret sharing scheme that KGC can broadcast group key information to all group members at once and only authorized group members can recover the group key; but unauthorized users cannot recover the group key. The confidentiality of this transformation is information theoretically secure. We also provide authentication for transporting this group key. Goals and security threats of our proposed group key transfer protocol will be analyzed in detail. This protocol can resist potential attacks and also reduce the overhead of system implementation. For securing storage and sharing of data on distributed storage sensor nodes while retaining data confidentiality, sensor nodes encrypt their collected data using ABE public keys and store encrypted data on storage nodes. Authorized users are given corresponding decryption keys to read data. The main challenge in this case is that sensor nodes are extremely resource-constrained and can just afford limited computation/communication load. Taking this into account we divide the lifetime of sensor nodes into phases and distribute the computation tasks into each phase. We also revised the original ABE scheme to make the overhead pertained to user revocation minimal for sensor nodes.