Efficient MAC enforcement approach for intruders in commercial operating system
Our Price
₹2,500.00
10000 in stock
Support
Ready to Ship
Description
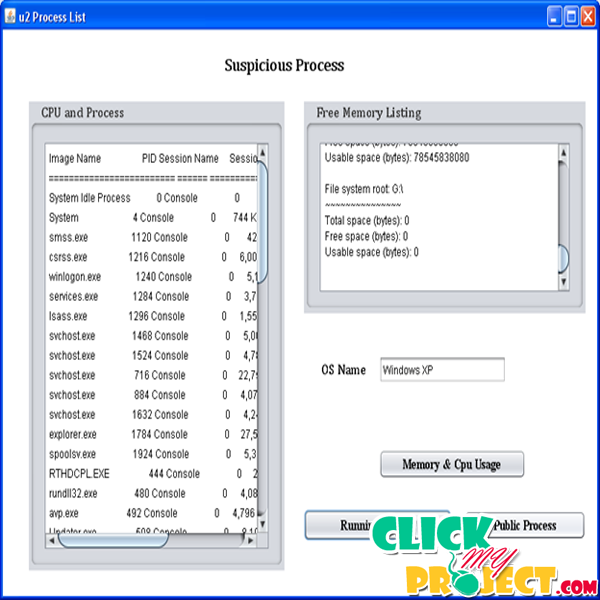
When malware is present inside the operating system the MAC works to prevent them but resulting the damage of system. Even if an intruder manages to breach other layers of defense, MAC is able to act as the last shelter to prevent the entire host from being compromised. We propose a novel technique called tracer which incorporates intrusion detection and tracing in a commercial operating system. The approach conceptually consists of three actions: detecting, tracing, and restricting suspected intruders. MAC races intruders and restricts only their critical malware behaviors, where intruders represent processes and executables that are potential agents of a remote attacker. Meanwhile, it permits suspicious processes to run as long as possible but only forbids their malware behaviors.
Tags: 2012, Java, Security Projects