Detection and Localization of Multiple Spoofing Attackers in Wireless Networks
₹2,500.00
10000 in stock
SupportDescription
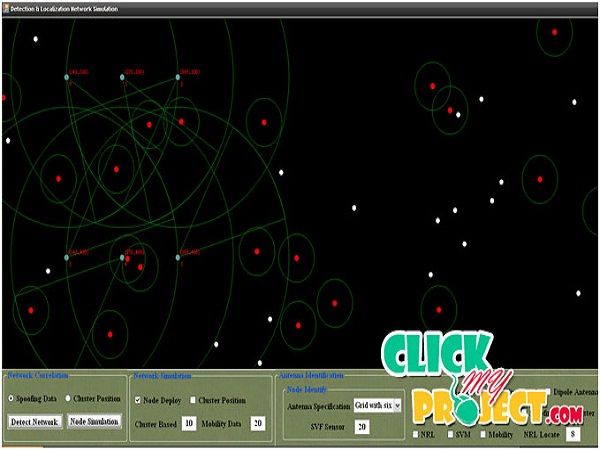
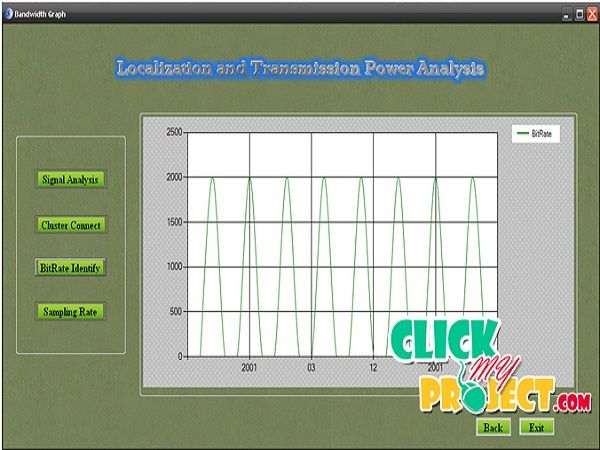
• Wireless spoofing attacks are easy to launch and can significantly impact the performance of networks. • The identity of a node can be verified through cryptographic authentication, conventional security approaches are not always desirable because of their overhead requirements. • The ability to identity based attacks in which a malicious device uses forged MAC addresses to masquerade as a specific client or to create multiple illegitimate identities. • The network is able to robustly identify each transmitter independently of packet contents, allowing detection of a large class of identity-based attacks with high probability. • The attacker can listen to all wireless traffic, compromise encryption and Use attenuators, amplifiers, directional antennas, software radios, but he cannot be at the location of user or at the location of access points. • The spatial correlation of received signal strength (RSS) inherited from wireless nodes to detect the spoofing attacks. • In experimental results show that our proposed methods can achieve over 90% Hit Rate and Precision when determining the number of attackers. • localization results using a representative set of algorithms provide strong evidence of high accuracy of localizing multiple adversaries.